Are you new to proxies? Confused about the technical terms?
Don’t worry! This guide is a comprehensive one and will explain everything related to the proxies, so that you benefit from their useful technology.
After reading this post you’ll be able to differentiate between the various types of proxies and choose one according to your needs. People use proxies mainly because they want to surf the web anonymously and without any restrictions. To understand the proxies in a better way, we’ll start with its definition and the different types of proxies that are used.
What is a proxy?
A proxy is a middleman or an intermediary that connects your computer to the internet. So, when a user enters a web address in the browser, the proxy connects to the server and sends request for the information. The information related to the whole browsing session is then passed through the proxy and it reaches the client in the form of a text, picture, audio, or video. You can consider the proxy as a bridge that connects two things for maintaining a path or cycle. Thus, proxy is a useful technology that allows you to access the information from the internet.
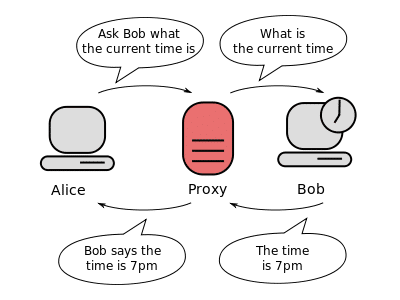
A proxy is used by most of the people to hide their identities such as the IP and MAC address so that they can surf on the web anonymously. If you want to bypass geological restrictions or censorship to access the content of a website, proxies are the best choice. Proxies will allow you to surf on the web anonymously and you can easily perform various activities on the internet without revealing your identity. This happens because the service provider offers you proxies with different geological locations so that your real location can’t be traced, and you can surf the web from other locations.
How does a proxy server work?
Now that you know that a proxy is an intermediary and it connects your computer to the internet so that you can access the information, we’ll explain how all this happens. For example, when you use a search engine, you enter a particular word or sentence in the search bar. This information is used as a request by the proxy and it is transferred to the server where it is processed. The information is then returned to the proxy which then reaches your computer. You might think this a lengthy process, but it takes only milliseconds for this process to be completed.
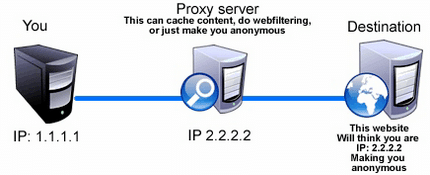
The proxy transfers the request and gets the response message from the server. Then it filters out the data such as your IP address so that your anonymity is maintained. This is the main difference between a proxy and a direct internet connection. Proxies have simplified the task of information gathering and complex methods of researching. Using these proxies, people can easily look up for the information they want on the internet and maintain their anonymity while they’re surfing the web. Following are the steps that will explain the manner in which the proxies work:
- A proxy analyzes the local cache and makes sure whether the request for a particular web page can be processed or not.
- The proxy sends the request to the proxy server and the server sends a respond message. In doing so, the proxy doesn’t use your IP but act as a client on your behalf.
- If the proxy couldn’t locate the web page present in its local cache, it will send an error message. If the request is fulfilled, it is responds positively and the web page appears on the browser.
What are the advantages of proxies?
Proxies can be used for a variety of purposes starting from basic internet activities to performing important tasks such as data scraping or doing transactions. Proxy is basically an application-level gateway that acts as a bridge between the huge world of internet and the user. Taking that definition in mind, we’ll discuss the benefits of using proxies. Here are some advantages of using proxies:
Malicious websites are filtered out
Proxies offer a secure way to surf on the web. This is because they act as filters for all the malicious content out there such as malware and viruses. The admin can easily block those websites that are dangerous for the system. The admin can also analyze phishing links and know which websites are malicious or contain malware. They can easily block those websites before the users access the websites. If the users accidentally land on a malicious website, they might have their whole system affected due to the infection.
IP address is hidden
The biggest benefit of using proxies is that the IP address remains hidden no matter what type of activities you perform on the internet. Normally, when you use a website, the website can easily log your real IP address and know about your details such as your location. However, proxies don’t allow the websites to know about the IP address as they mask it. The website will be able to detect the proxy server’s IP address which may be present at some other location.
IP address is an important thing which has all the information regarding your identity, and it can reveal the country from which you’re using the web. Proxies prevent this from happening and mask your IP address so that you can surf the web freely and anonymously.
Bypass geological restrictions and censorship
If you own an international business, it gets difficult to know about the interest of people from other countries because of the geological restrictions. There are many websites that allow only people from certain countries to view the content. In such case, proxies prove to be very useful because they can help you bypass such restrictions. You can also use proxies to show your business’s website content depending on the country of the visitors. Proxies also help to bypass censorship which some website owners place on their websites for particular types of visitors due to certain reasons.
Anonymity and protection:
If you don’t use a proxy as a middleman and access a website directly, you’re surfing the web at a low security level. This way hackers can easily access your information and use it for performing illegal activities on the web. Also, it is very risky to do online shopping and perform transactions because there is a chance of the information being leaked. Proxies provide protection to such activities because they hide the IP address from everyone. Your IP address is hidden from the external servers and thus you are safe from any type of malicious activities. Some good proxy providers also offer a firewall as an additional protection to their users.
Reduction of load time
Proxy servers can cache data, which means that they can save the pages for later use. When a proxy accesses a web page, it makes it appear on the web browser and then saves it in the cache. When the user requests that page again, the proxy displays it from the cache and this causes a reduction in the load time. This happens only when the page has been once visited by the user, because then only it will be saved in the cache by the proxy. If the page isn’t present in the cache, it will take similar load time as other pages normally take for loading.
Types of proxies
There are many different types of proxies but broadly they are divided into two categories. The proxies are further divided into many categories which we’ll discuss in detail too. Following are the main types of proxies:
HTTP proxies
HTTP (Hyper Text Transfer Protocol) proxies are used for transferring and displaying files on the internet, which include anything such as text, images, audio, and video. These proxies act as content filters and they check the web traffic so that all the malicious or suspicious content is filtered. HTTP proxies configure only those web pages that comply with the RFC specifications or are related to a verified source. These proxies also block the downloads that are of particular file types.
The HTTP proxies work as both, the client and the server. The HTTP client sends the request message to the HTTP server, which then processes the request and sends a response message if the request is fulfilled. If the request isn’t fulfilled, the server sends an error message. The HTTP proxies are smart, and they can interpret the data that is being sent and received through them. These proxies operate at a higher level and are one of the most used ones on the web.
HTTPS proxies
The HTTPS proxies are actually the HTTP proxies with a ‘Secure’ option. If you have to perform a sensitive task which involves confidential information, you can use the HTTPS protocol to do so. You can easily upgrade your HTTP proxy to HTTPS and that will add an extra layer of security to your internet activities. However, upgrading to HTTPS is only necessary when you have to perform highly confidential tasks such as bank credit info or others.
SOCKS proxies
The SOCKS (Socket Secure) proxies are secure proxies and they are quite different from other proxies in terms of functionality and performance. HTTP proxies take your request to the server and establish an internet connection, while the SOCKS proxies establish a proxy connection after exchange of messages. A SOCKS server establishes a TCP connection on behalf of the client and exchanges the data to and from the client. The data that is transferred between the client and the server can’t be interpreted by the SOCKS proxies because they aren’t smart as compared to the HTTP proxies.
Since SOCKS proxies are not very smart or intelligent, they are more secure as compared to the HTTP proxies. The SOCKS proxies give more anonymity to the user and maintain privacy by not penetrating the data. SOCKS proxies are used when the clients behind the firewall are not allowed to use TCP connections to the servers that are present outside the firewall. Using a SOCKS server, you can configure a web browser to communicate with the web server easily.
Main points defining the use of SOCKS proxies
When you’re using SOCKS proxies, you’re basically using a general-purpose connection that is established to route the traffic between the client and the server. Following are the main points that define the properties of SOCKS proxies:
- They are not intelligent or smart and thus they can’t read or interpret the data that is being communicated between the client and the server.
- Unlike the HTTP proxies, they can work with any type of connection. This means that there are no compatibility issues with these proxies and you can use them with HTTP, FTP, SMTP and even POP3.
- They operate at level 5 of the OSI model and only authorized users can access them.
- SOCKS proxies act as client because it adds nothing from itself while the data is being transferred from the client to the server.
- SOCKS proxies can be used to create a chain. This can be possible when a proxy establishes a connection to another different one and so on.
Variants of SOCKS proxies
SOCKS proxies route the network traffic between the client and the server using a proxy server. SOCKS proxies are of two different types, and they can be used according to the level of security needed. Following are the two main variants of the SOCKS proxies:
SOCKS 4
SOCKS 4 is the variant of SOCKS proxy that supports only the TCP connection. SOCKS 4 proxies are basically SOCKS proxies in general that don’t support other authentication mechanisms and DNS.
SOCKS 5
The SOCKS 5 proxies are more secure and more advanced versions of the SOCKS proxies. They support TCP and UDP applications both and also support the Domain Name Resolution (DNS) and different authentication mechanisms. SOCKS 5 is very secure and if you want added security, you can use SOCKS 5 proxy to make sure your sensitive information is well protected.
Free proxies vs Private Proxies
You may be note, there are lots of free and paid proxies online, what's the different between the Free proxies and Private Proxies? Let me discuss about it,
Public/free proxies
Free or public proxies are available free of cost and thus they are the cheapest option if we compare them to other proxies. Since the public proxies are free, they are accessed by multiple users at the same time. This causes the speed to slow down and the internet users face very low speed or no network most of the times. The free proxies are not recommended for using social media accounts or performing other activities that require login details such as usernames and passwords. These proxies are not secure as there are many people using it, there is a chance that the information can easily be stolen by hackers.
Shared/semi-dedicated proxies
Shared proxies are the ones accessed by fewer users. For example, if the free proxies are accessed by thousands of users at once, these proxies are being used by hundreds of people simultaneously. The speed is better than free proxies because they are not as many people accessing the proxy. The shared proxies are more secure as compared to the public proxies, and if you choose a premium service provider, you’ll get a good service in terms of speed, security, and overall performance. These proxies are available at a price, but they are very affordable. If you’re on a budget you can use these proxies to surf on the web.
Private/dedicated proxies
The private proxies are the most secure ones, but they are also the most expensive ones as well. With the shared proxies, the cost is divided among the number of users and thus it is very less. However, the private or dedicated proxy is setup especially for a particular client and he/she has to pay for it completely. Though this is an expensive option, a private proxy is the best in terms of speed and security. Most of the proxy service providers will use latest technology to provide additional security and make sure that there is no speed drop either. If you have highly confidential tasks to do, you can use the private proxies to surf anonymously on the web.
How to choose a port for the proxies?
Choosing a port is an important thing to do after you have bought the proxies. To setup the proxy in the browser, you’ll need a port and it will play an important role in improving your browsing experience. Most of the people don’t understand the importance of ports for proxies and they use one port for all types of proxies. This creates problem such as inability to connect or other difficulties in getting online. To understand what a proxy port is, read more.
A computer consists of many different ports that are used for various tasks. The ports are not present in a physical form, in fact they are present virtually and have been assigned particular numbers so that you can access them easily. Basically, when you set up a proxy, you assign it a port which gives it the access to the information inside your system. This is imperative if you’re going to connect to the internet using your proxy.
The HTTP proxies can be set up using the 80 port, while the HTTPS should be setup through port 443. As mentioned earlier, the SOCKS proxies can be setup using any port as they don’t have any compatibility issues. The default port for SOCKS proxies is 1080 but you can use any port for configuration. If you are confused regarding the use of ports for setting up the proxies, try configuring through any port and then check whether you’re able to go online or not. If you aren’t able to connect, it means you need to use a different port for setting up a particular proxy on the browser.
Conclusion
Choosing the type of proxy depends entirely on you, and the nature of the task that you’re going to perform. Free proxies should be used only for basic internet surfing activities because they aren’t secure. If you don’t have any choice but to use the free or shared proxies, you can setup SOCKS proxies simultaneously so that you have an additional layer of security.



